blog
tags
posts
-
Detection Surface Series 5: The role of Threat Modeling
DRAFT
-
Detection Surface Series 4: Detection Surface

-
Detection Surface Series 3: Design for Prevention Avoid Detecting Entirely
-
Detection Surface Series 2: Security Relevancy as an enabler of Visibility
Let’s consider the following thought experiment:
 Imagine an information system, where we don’t use any database for storing information, instead a system, where logging is replacing databases, and granular level permissions can be added to logs as well. After every action of an information system, we would create a logline, which may or may not be visible to different users:
Imagine an information system, where we don’t use any database for storing information, instead a system, where logging is replacing databases, and granular level permissions can be added to logs as well. After every action of an information system, we would create a logline, which may or may not be visible to different users:- the application administrator would see everything including the code and the logs
- the logging administrator would see all logs and the code that specifically generates the logs (similar to a DBA in the normal world)
- a group owner would see the actions performed in the group by all accounts, but not others
- the owner of an account would see the actions performed by that account only
- the application would be able to read the logs needed for it’s own functionality, but not things that are meant to be private
- the security administrator would be able to see everything in the
security log- security controls added, such as a new MFA device added by a user
- the salted & hashed values of passwords,
- login details of everyone,
- known attacks carried out against the system,
- symmetrically encrypted protected information,
- fraudulent transactions performed by potentially the same person, using both the initiating user and authorizer user of a payment, connected from the same IP address with only minutes delay
- new users being created by unusual, highly privileged accounts
- a library function with a recently discovered vulnerability being called to handle an uploaded file, hence potentially endangering the system integrity.
- a configuration change that removes a security control, making resources openly accessible
- a third party API returning unusual, un-sanitized input, due to being trusted by default(when no API input validation - similar to user input validation - has been implemented)
- objects being accessed out of ordinary bounds, due to broken access control / object level authorization
- a known vulnerable piece of the software is being run, and resulting in a permanent connection, and system level access through remote code execution
- etc.
-
Detection Surface Series 1: Loggable to Detectable
The basic activity diagram of security logging is as follows:
 Note that there are many steps involved in this process. It all starts with, “do we even really want to log and monitor this activity?”
In a hypothetical world, a security professional’s dream answer would be, “Yes, and every single action that may represent a
Note that there are many steps involved in this process. It all starts with, “do we even really want to log and monitor this activity?”
In a hypothetical world, a security professional’s dream answer would be, “Yes, and every single action that may represent a security relevantevent should indeed be logged.” -
Best Email Privacy and Productivity Tips for 2024
One practical step towards a more responsible digital life - that you can take in a few minutes - is to use email aliases when registering to services. It will help you to protect your primary email address that you care about, simplify your online presence(no need for multiple throwaway emails), knowing which contacts might have been misusing your data and recognise phishing much easier.

-
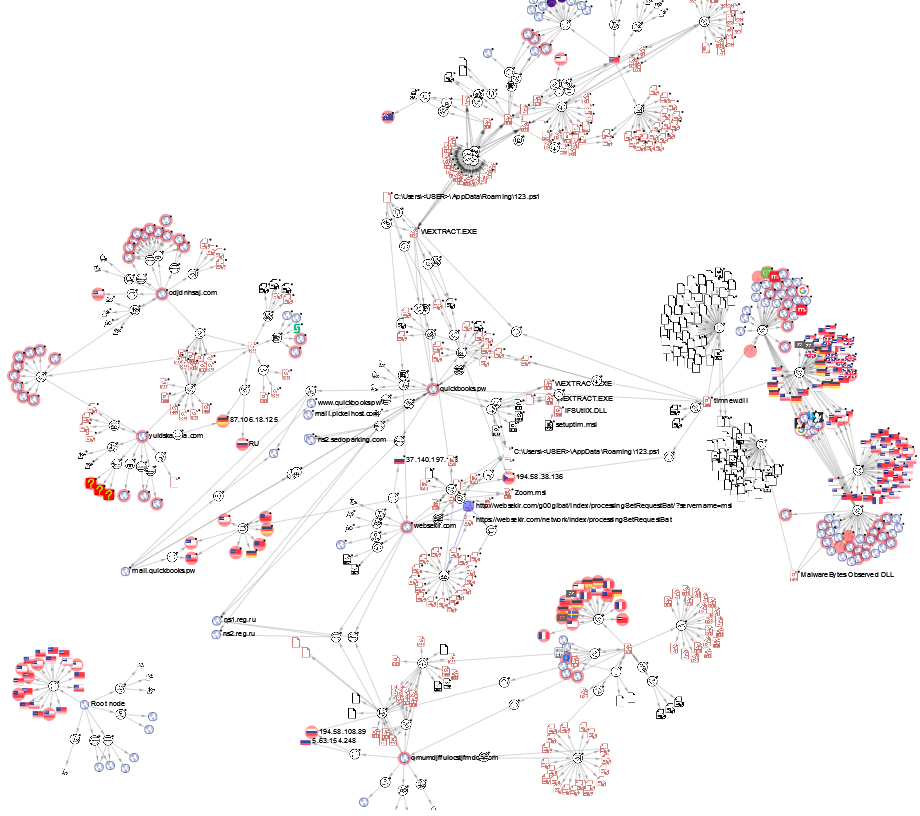
Malware Analysis - Zloader
Campaign Information
In 2021 September, I came across a (then) recent sample for Zloader. After finishing with most of the static analysis steps, I noticed there is already existing research on this by SentinelOne, but I thought carrying on with the analysis will be good practice and use of my time.
-
Book Review - Incident Response Techniques for Ransomware Attacks
A comprehensive Ransomware Tactics summary with a wealth of Digital Forensics insights 🔍
Understand modern ransomware attacks and build an incident response strategy to work through them - by Oleg Skulkin
